Service Management
In control of security and compliance
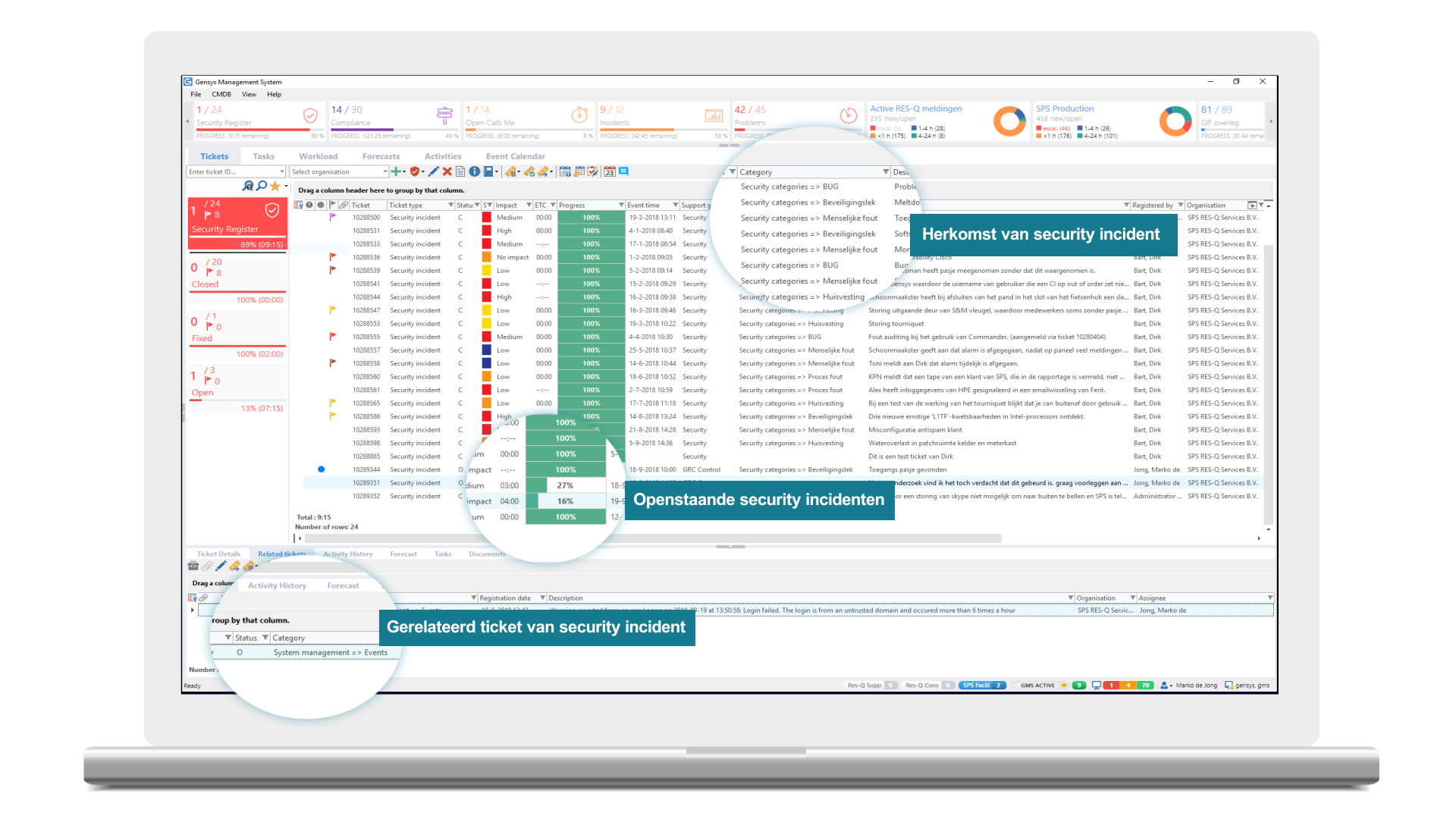
Record security incidents in the security incident register or, as the case may be, in the data breach register. Ensure that security incidents are handled by the Security Incident Response Team. Escalate when required. Assign recovery tasks and maintain control. Report on many viewpoints, such as risk, threat, impact etc. Communicate incident and status with adjacent software, including GRCcontrol.
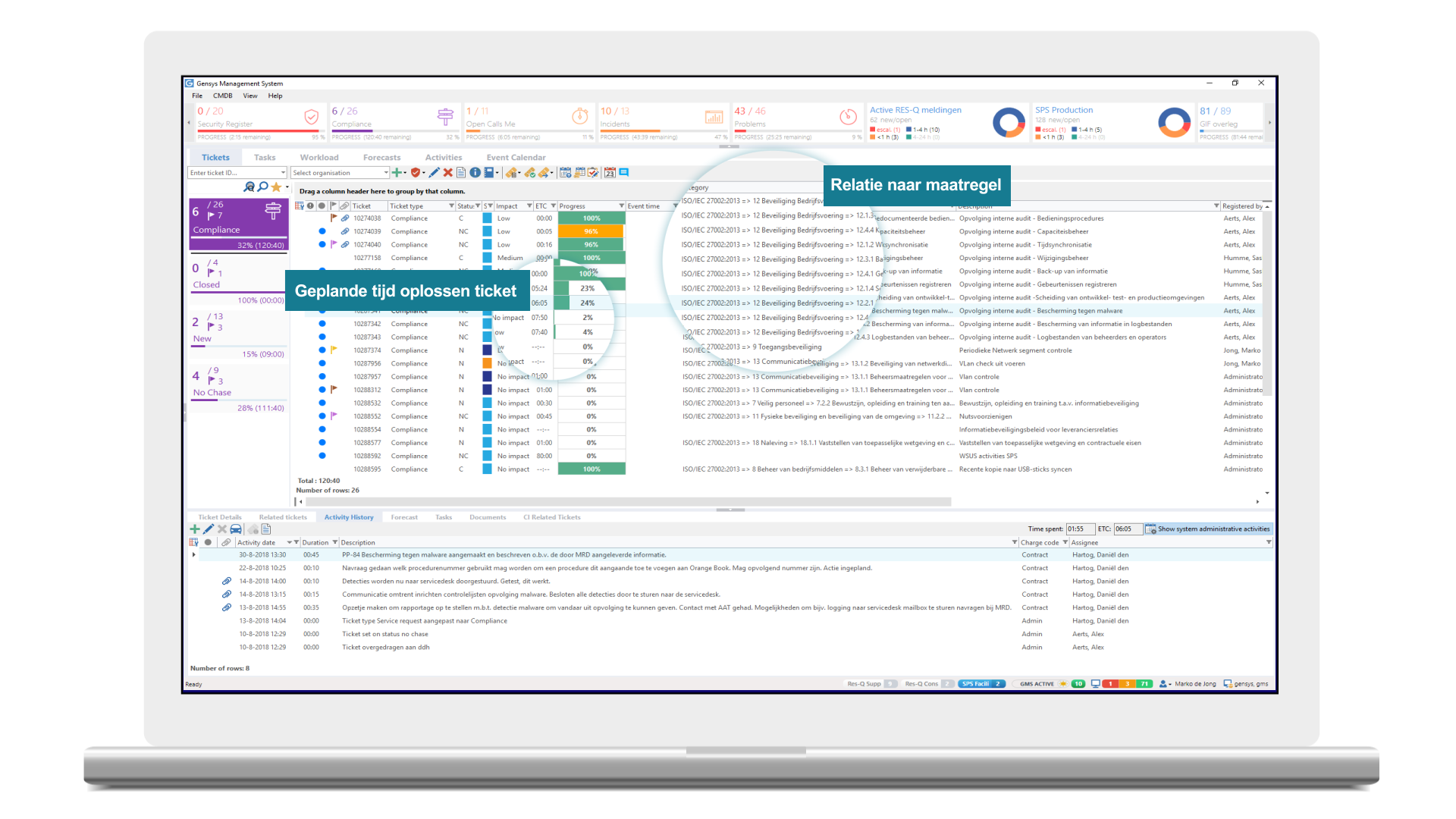
Establish compliance measures from standards. Plan those measures in the future and be sure that tasks are being assigned. Demonstrate at any time that compliance measures have been or are yet to be implemented. Acquire the evidence for audits and claims. Significantly reduce the effort required to manage compliance.
Treat security incidents appropriately
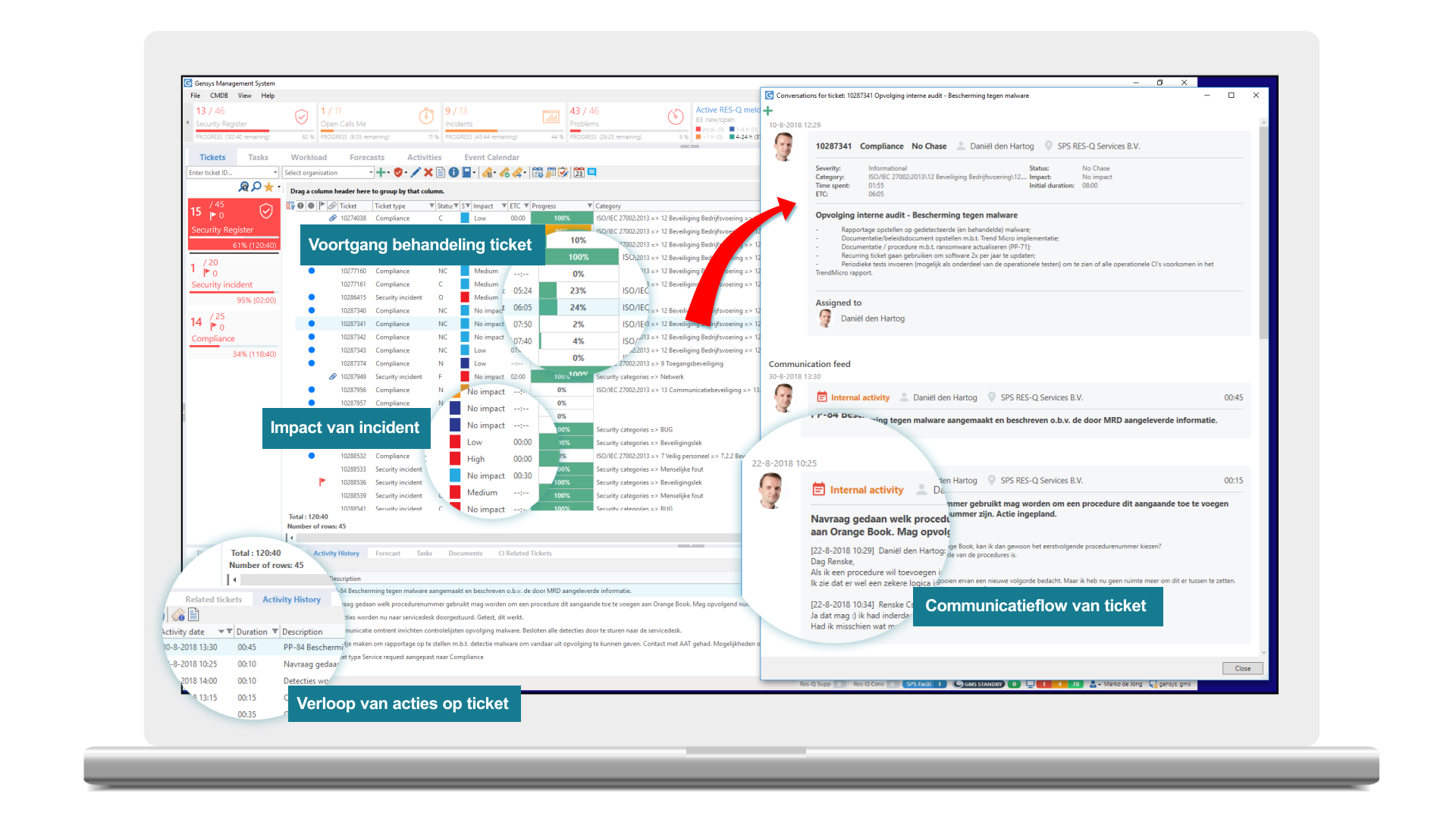
Handle security incidents according to the rules, with the right priority and by qualified employees. Record security incidents in the secure security incident register, accessible only to the Security Incident Response Team (SIRT). The SIRT assesses and analyses security incidents and assigns corrective and preventive tasks to administrators and managers. The SIRT remains in control until the tasks have been performed satisfactorily. Link security incidents to a Service Level Agreement and monitor their handling with automatic escalation when criteria are exceeded. See at any time the current status of security incidents, what still needs to be done and who is responsible for the execution of tasks. Categorise security incidents by their origin for instance, and classify them to indicate the risk, type of threat or potential impact, among other things. Make audits and evidence simple with comprehensive reports differentiated by categorisation and classification.
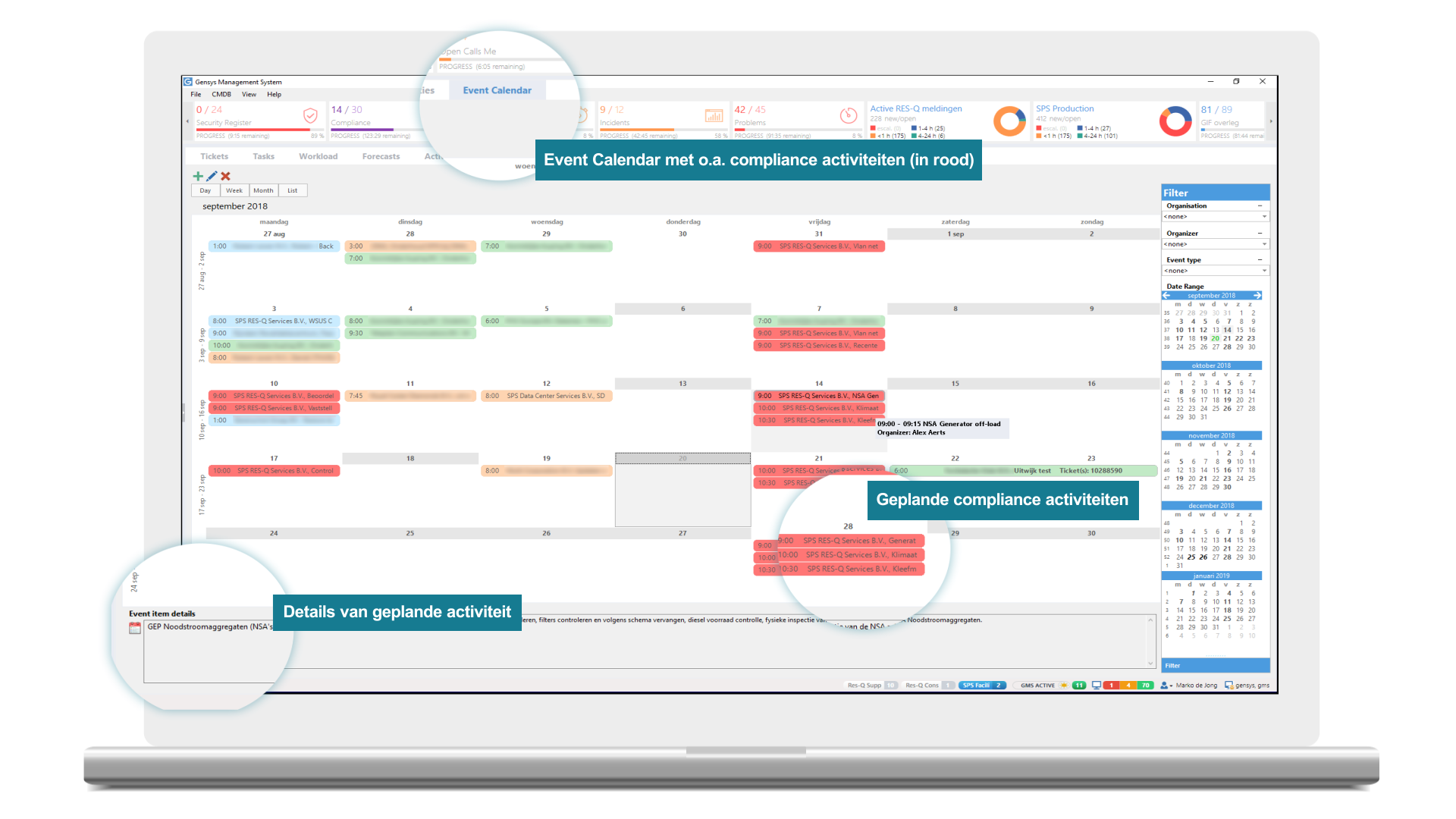
Ensure implementation of compliance measures
Obtain assurance that compliance activities are performed on time and adequately. Link the activities to measures of standards, for example ISO27002. Implement relevant parts of the Statement of Applicability (SoA) and plan activities, with tasks for administrators and managers, at the prescribed frequency. Ensure that tasks are performed on time and by the right people. Monitor execution with an SLA and see the completion of tasks and workload in real-time. Easily gather evidence that compliance measures have been implemented and the SoA is being complied with.
Integrate policies with operations
Register IT-related security incidents and compliance activities in Gensys. Manage their handling and execution with Gensys. The operation is under the control of Gensys. If you opt for special software, such as GRCcontrol from CompLions, to safeguard information security demonstrably as a process, including recording measure implementations, Gensys communicates with this software through APIs. Security incidents are continued for, among other things, risk assessment, incident management, reporting and testing with the policy and the measures derived from it. The external software can send tasks to Gensys following the security incident, but also autonomously. Gensys monitors their execution and the status of incidents is synchronised.
In control of security and compliance
Gain real-time visibility into the security incident register. Be assured that security incidents are handled on time by the right people. Assign the direction of security incidents to the right people responsible, the SIRT. Save a lot of time managing compliance activities. Easily obtain adequate evidence for audits and claims. Demonstrate at any time that compliance measures, derived from standards, have been executed correctly and on time. Take security issues and compliance seriously. Make sure you’re in control of security and compliance.
Make sure that you are ‘in control’ of security and compliance. Check the brochure.

“Our customers also benefit from Gensys’ Service Management solution”
Tim Doets, Business Development Manager